Lovelinks.us spam adverts on Android devices
What should have been a few relaxing minutes with (non Dana White approved) MMA related news on my Nexus 4, was soon to be turned into a browser hijacking battle courtesy of lovelink.us.
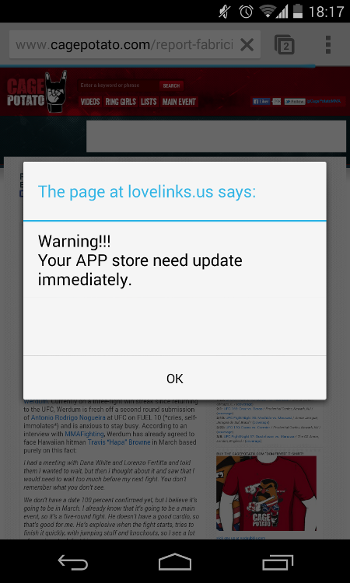
Nexus 4 running Android 4.4.2
What makes this crapware especially annoying is its ability to hijack the Chrome browser and force the user into Google Play to (hopefully) buy a promoted app.
I did some googling and noticed that this kind of spam is usually attributed to dishonest apps on your phone and the subsequent advice is to install some antivirus tool to clean your phone.
In my case, I was pretty confident that this was not the case so I decided to see if i could find the culprit. Obviously this was not something easily conducted on an Android device so I decided to use Chrome Canary on the Windows platform instead, to make use of the included developer tools. Chrome Canary is able to emulate the exact environment from my Nexus phone, so I should be able to reproduce the spam message on my desktop computer if my suspicions were to be confirmed.
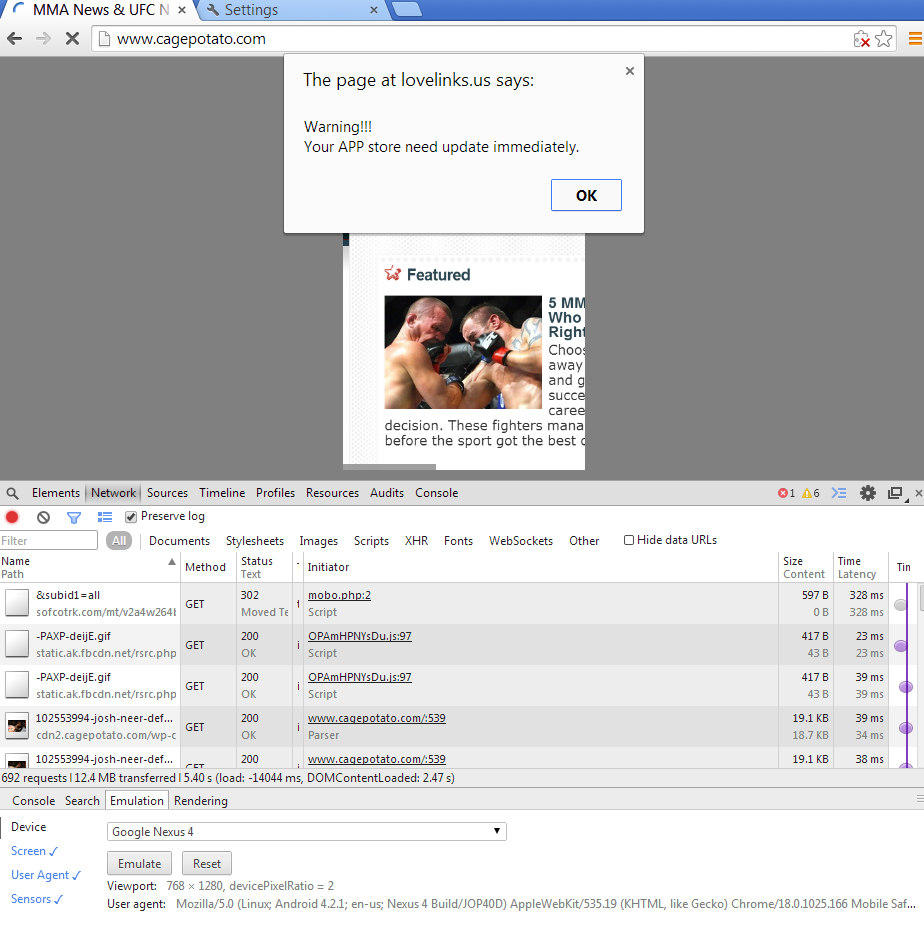
After setting up Chrome Canary and loading the site in question, it didn’t take long before I was greeted by the same spam message.
By using the developer tools it was only a matter of browsing through the loaded scripts to identify the culprit.
A bit simplified and shortened, the code execution is as follows.
Load the popup and redirect the user to mobo.php regardless of user confirmation or exit.
<script>
if(self!=top)
{
window.open(self.location,'_top');
}
</script>
<script type="text/javascript">
alert("Warning!!!\n\Your APP store need update immediately.");
</script>
</style><script type="text/javascript">
document.location.href = "mobo.php";
</script>The user then gets redirected to sofcotrk.com which in turns loads the Google play store with their suggested app.
</style><script type="text/javascript">
document.location.href = "hxxp://sofcotrk.com/mt/v2a4w264b4y233r244z2u2b4/&subid1=all";
</script>There is nothing sophisticated about this at all, but it’s made possible due to Google’s lack of available security features in Chrome mobile.
Obviously Google does not favor giving their users the freedom to block ads, as the removal of AdBlock from Google Play suggests.
This kind of crap is exactly the reason why I don’t trust advertising networks and given the choice, I always opt out. Security concerned users are also aware that third party advertising is a big risk factor for drive by exploits.
And for the icing on the cake, Google’s developer tools is also capable of showing the initiator behind injecting the lovelinks.us crap.
In this case, that would be ads.yahoo.com. Would this be the same Yahoo which infected their own users with malware recently I wonder.
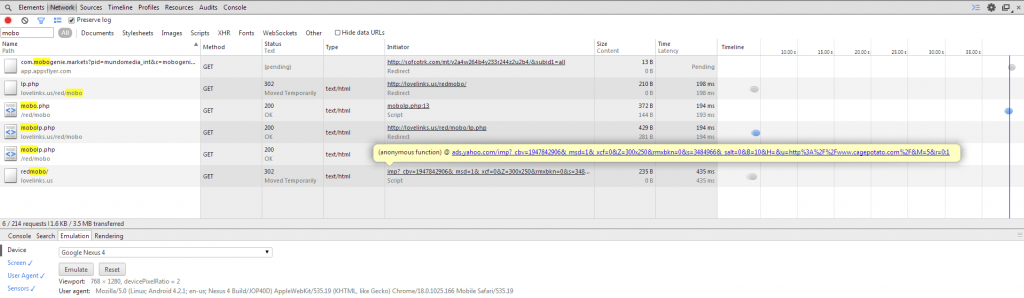
Lovelinks.us spam- courtesy of ads.yahoo.com
